Scam and Malicious APK targeting Indonesian, pretended as delivery service— A malware analysis
Overview
I had a chat with some of anonymous friends in the group, we talks about the cyber criminal case targeting Indonesian recently. One of my friend then share the Application Packaging Kit (APK) file to analyze together, to see what really happened behind the case. As we know, currently, even tough some of the criminal member already arrested but there are no technical information released so far.
So the malware sample detail information is appear bellow:
MD5 Hash : 4f3308d37f2575d418e24464d980a718
Filename : Pos Indonesia.apk
File Type : Application Packaging Kit (APK)
App Name : Pos Indonesia
Package Name : com.pos.indonesia
Main Activity : com.example.myapplication.MainActivity
Android Version Name : 1.0
Android Version Code : 1
Target SDK : 32
Min SDK : 26
Attack Overview:
- Attacker has leaked file of a bank customers, it could be from dark web or corrupted employee sells the files.
- Attacker then randomly sent phishing over Whatsapp and wait for any reply from victims.
- Victims then installed the malware and unable to uninstall since not listed on application list on their phone.
- When attacker tried to reset password when tried to login to victim bank account, it sent OTP SMS to victim phone, which then copied and forwarded to a Telegram bot URL by the malware.
- Attacker then successfully reset password for victim’s account from attacker device.
- And finally gain full access to victims account and made valid transaction approved by the bank’s system.
Even though, this only cover the static part but we can guess the flow by installing the malware on testing device and see the behaviour aligned with the source code.
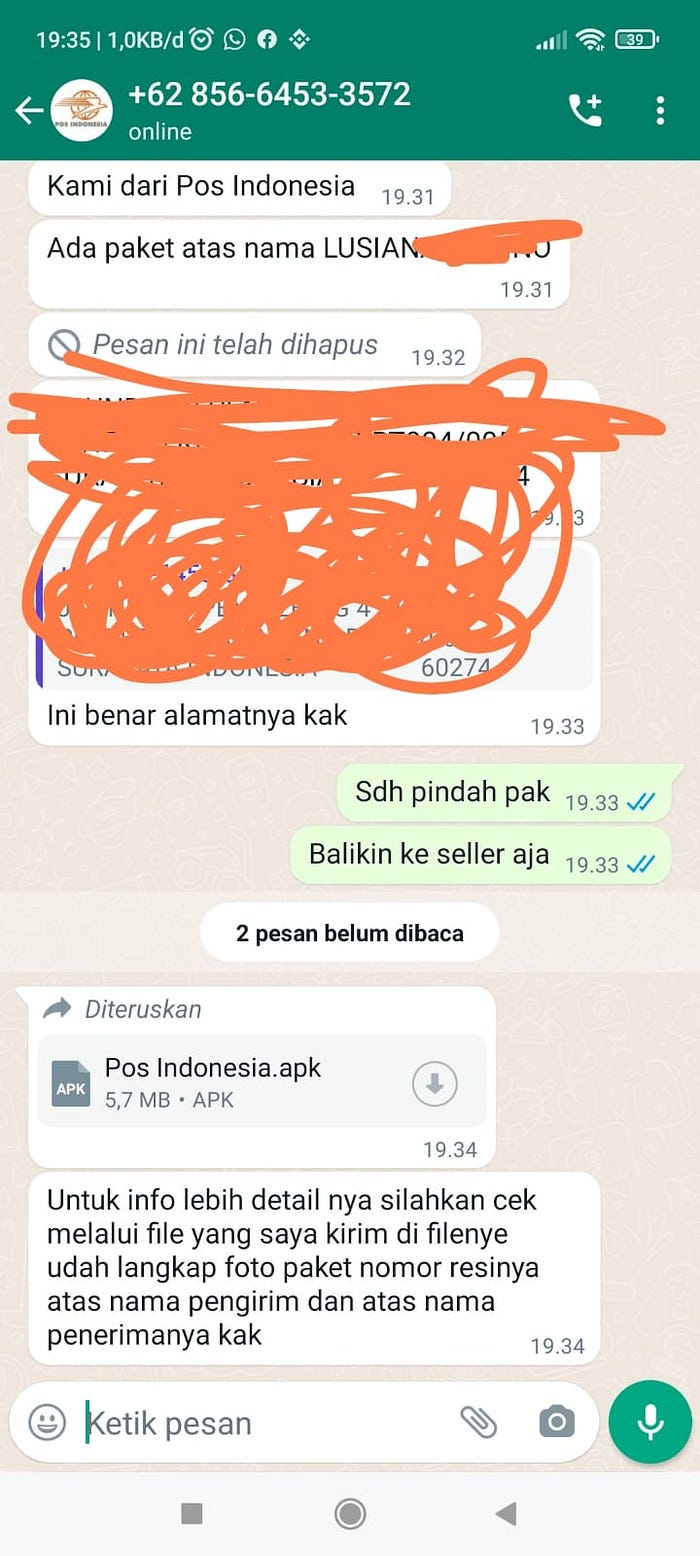
Static Analytic
So, this article only cover the static part of analytic, while the dynamic part will be uploaded later.
When I check the Manifest file, it shows that this application required Internet and full SMS uses-permissions to run.
Whit these permissions, this malware able to open internet socket, read, write, delete and send SMS with no victim control
$ grep "android.permis" kurir-apk-out/AndroidManifest.xml
<uses-permission android:name="android.permission.RECEIVE_SMS"/>
<uses-permission android:name="android.permission.INTERNET"/>
<uses-permission android:name="android.permission.READ_SMS"/>
<uses-permission android:name="android.permission.SEND_SMS"/>Full script of MainActivity.java is:
Based on MainAcvifity.java file above, when this malware installed, it will check for gather information of the device (line 26), then checking for permission. Is it allowed or not, and then sent the result to a Telegram bot (line 58), so attacker will gather the list of potential victims based on these information.
Then it will automatically open this URL https://www.posindonesia.co.id/id/content/aplikasi-posaja with a webview component, so victim will think that this application is real.

After victim close the webview component provided URL by the malware, this malware then hiding it self from application installed list on victim’s phone (line 112).
Telegram Bot
The bot called several time on the files, each action would reported to attacker channel, and they will sort the potential victim based on device information, which were vulnerable and responded to phishing attacks.
Conclusion
This attack only happens when victim allowed unknown source to be installed on their Android phone. Make sure to lock this action from being modified with a password or pattern security for confirmation. Otherwise, buy an iPhone, which not considerable as 100% safe, but at least this type of attack not applied on it since most of attacker were targeting Android phone. There are some antivirus available for mobile phone, Malwarebytes for example, this one can is recommended for a protection.
Related sources
- https://indonesia.postsen.com/local/446320/Police-reveal-APK-modification-syndicate-and-phishing-links.html
https://rm.id/baca-berita/megapolitan/157507/dittipidsiber-bareskrim-bongkar-penipuan-berkedok-modifikasi-android-package-kit
